Use our free tools to begin your shortlist,
while exploring technical demos and in-depth product analysis.
The DSPM marketplace is 100% funded by our vendors.
When contacting vendors we ask that you please use our platform.
Doing so provides continuous support for the platform and allows us to expand our library of free services
DISCOVER
Explore the list of DSPM solution providers
LEARN
Learn from the best with technology deep-dives
EVALUATE
Compare products and providers side by side
CONNECT
Contact DSPM vendors to book a live demo

Cyera's data security solution can be up and running within minutes, harnessing advanced machine learning and automation to diminish access vulnerability. It guarantees the secure storage of sensitive data while effectively managing data sprawl, ultimately optimizing overall data security.
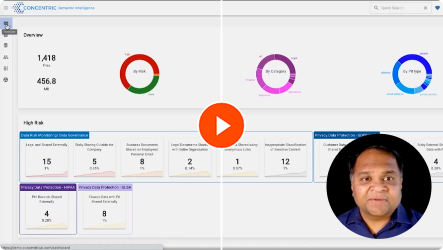
Karthik Krishnan, the CEO of Concentric AI, guides us through their DSPM offering, demonstrating its utilization of deep learning to classify data, evaluate potential risks, and resolve security concerns. Operating as an agentless platform, Concentric AI's Data Security Posture Management solution can be effortlessly deployed to categorize data and pinpoint risks.
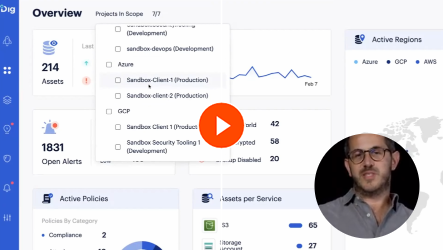
Dig Security offers a potent and complete platform that uniquely integrates DSPM and DDR. This synergy delivers real-time data risk visibility across multiple public cloud environments, facilitating rapid identification, classification, and prioritization of data risks.

The Laminar data security platform empowers organizations with essential visibility, precise control, and adaptable agility, enabling them to establish robust security, privacy, and governance measures that align seamlessly with the rapid pace of technological innovation.
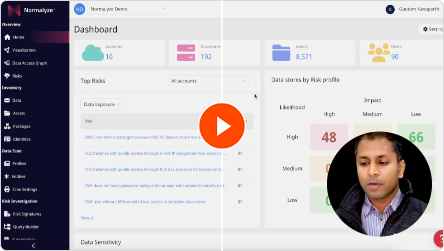
Engage in a practical demonstration that illustrates how Normalyze effectively addresses the primary data-centric security hurdles prevalent in contemporary cloud environments. This includes tasks such as data discovery, classification, access governance, risk identification, and compliance enforcement.
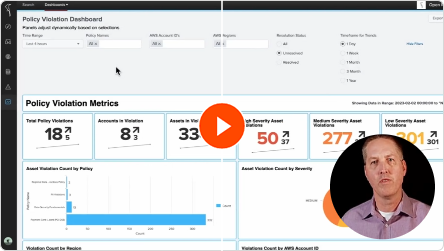
David Gadoury, Senior Solutions Engineer, delivers a technical showcase of the fundamental functionalities within the Open Raven Data Security Platform. This demo includes identifying and categorizing unstructured and structured data, generating a comprehensive data catalog, implementing rules and policies, and setting up integrations and reports.

Richard Stiennon, Anto Chuvakin, and Bard LaPorte explore the driving forces behind innovation in DSPM technology while offering valuable insights and guidance to users participating in the DSPM Demo Forum.
Explore DSPM through Technical Demos and Expert Presentations
Click on the provider's logo to visit their Demo Room.
Our library is continuously expanding with the lastest technology demos and discussions, ensuring you have access to the freshest insights and innovations in the cybersecurity realm
Interested in listing your company's services on our website?
Fill out this form and tell us about the services your business offers.
Cyera offers businesses an immediate comprehensive insight into their sensitive data and security vulnerabilities. It employs automated remediation to minimize their potential attack surface and enhance their ability to withstand cyber threats.
Karthik Krishnan, the Chief Executive Officer of Concentric AI, talks with Richard Stiennon, delving into data security trends, the realm of DSPM, and how Concentric AI's DSPM solution can effectively assist enterprises in safeguarding their both organized and unorganized data.
Dig Security's entirely agentless and cloud-native methodology amalgamates Data Security Posture Management (DSPM), Data Loss Prevention (DLP), and Data Detection & Response (DDR) within a unified platform. Experience a live demonstration by visiting dig.security.
Explore the significance of Data Security Posture Management (DSPM) and uncover how Laminar is playing a pivotal role in enabling organizations to acquire the essential visibility, authoritative control, and dynamic agility required to establish robust security, privacy, and governance measures.
Ravi Ithal, the Chief Technology Officer of Normalyze, teams up with Richard Stiennon to converse about DSPM and elucidate how Normalyze is actively assisting clients in reestablishing cloud data visibility, authoritative control, and a sense of trust.
Richard and Dave delve into the indispensability of DSPM, typical scenarios of its application, and how Open Raven effectively empowers security teams to address fundamental queries concerning cloud data. They also explore how the platform facilitates the imposition of security measures and the eradication of risks.